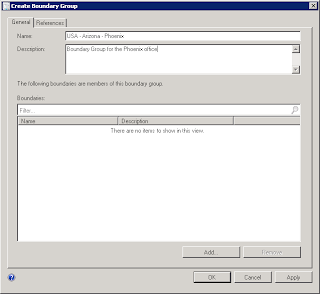
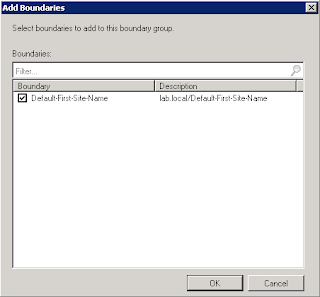
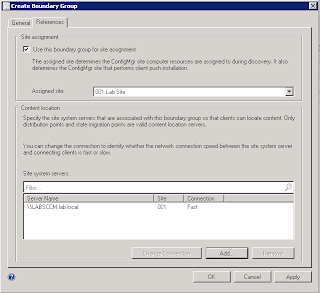
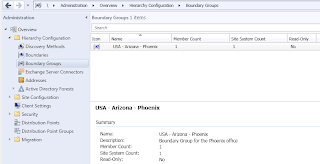
There are 18 total roles available in SCCM 2012. Upon installation and deployment of a new site several roles are installed by default. Additional roles can be added after deployment.
Site Server Roles (Default):
Configuration Manager site server - The site server role is automatically installed on your central administration site or primary sites. When you install a secondary site, the site server role is installed on the server that you specify as the secondary site server.
Configuration Manager site system - Site systems are computers that provide Configuration Manager functionality to a site. Each site system hosts one or more site system roles. This role is assigned during Configuration Manager site installation or when you add an optional site system role to another server.
Configuration Manager component site system role - Any site system that runs the SMS Executive service also installs the component site system role. This role is required to support other roles, such as a management point, and it is installed and removed with the other site system roles.
Configuration Manager site database server - A site system role that runs Microsoft SQL server and hosts the configuration Manager Site Database
SMS Provider - The SMS Provider is the interface between the Configuration Manager console and the site database. This role is installed when you install a central administration site or primary site. Secondary sites do not install the SMS Provider.
Site Server Roles (Optional):
Application Catalog web service point - A site system role that provides software information to the Application Catalog website from the Software Library.
Application Catalog website point - A site system role that provides users with a list of available software from the Application Catalog.
Asset Intelligence synchronization point - A site system role that connects to Microsoft to download Asset Intelligence catalog information and upload uncategorized titles so that they can be considered for future inclusion in the catalog.
Distribution point - A site system role that contains source files for clients to download, such as application content, software packages, software updates, operating system images, and boot images. You can control content distribution by using bandwidth, throttling, and scheduling options.
Fallback status point - A site system role that helps you monitor client installation and identify the clients that are unmanaged because they cannot communicate with their management point.
Management point - A site system role that provides policy and service location information to clients and receives configuration data from clients. You must install at least one management point at each primary site that manages clients, and at each secondary site where you want to provide a local point of contact for clients to obtain computer and user polices.
Endpoint Protection point - A site system role that Configuration Manager uses to accept the Endpoint Protection license terms and to configure the default membership for Microsoft Active Protection Service.
Enrollment point - A site system role that uses PKI certificates for Configuration Manager to enroll mobile devices and Mac computers, and to provision Intel AMT-based computers
Enrollment proxy point - A site system role that manages Configuration Manager enrollment requests from mobile devices and Mac computers.
Out of band service point - A site system role that provisions and configures Intel AMT-based computers for out of band management.
Reporting services point - A site system role that integrates with SQL Server Reporting Services to create and manage reports for Configuration Manager.
Software update point - A site system role that integrates with Windows Server Update Services (WSUS) to provide software updates to Configuration Manager clients.
State migration point - A site system role that stores user state data when a computer is migrated to a new operating system.
System Health Validator point - A site system role that validates Configuration Manager Network Access Protection (NAP) policies. It must be installed on a NAP health policy server.
Windows Intune connector - A site system role in Configuration Manager SP1 that uses Windows Intune to manage mobile devices in the Configuration Manager console.
Installing Roles:
Now that we know a little bit more about the types of roles that are available, lets go ahead and install the Application Catalog Web Service Point and Application Catalog Website Point roles. We need to make sure we add two additional IIS Role Services:
- Windows Authentication
- ASP.NET
The Add Site System Role wizard will open up. Click Next
Check Application Catalog Web Service Point and Application Catalog Website Point. Click Next
On the Application Catalog Web Service Point page you can define the IIS website and Website Application Name (URL) of the this site, it will be in http(s)://<servername>/<website application name> format. You can also determine if you want to use http or https. Click Next
On the Application Catalog Website Point page you can define IIS website, Website application name and http / https port similar to above but you can also define the site system server (the default in our case) and the NetBIOS name (also the default). Click Next
Here you can do a little bit of custom branding by providing your organization name and selecting a custom color theme (these can be changed later). Click Next
Review your settings and Click Next
You will get a success that the wizard has successfully kicked off the installation. You can review the progress of the install on the Monitoring space under System Status then Component Status. You can also review the install log <install directory>\Microsoft Configuration Manager\Logs\SMSPORTALWEBSetup.txt
When the install completes you should be able to navigate to http(s)://<servername>/<website application name> from a computer with Silverlight installed.
More to come!
If you like this blog, give it a g+1
Contributing documentation:
Technet