There are a few things you will need before we begin:
- SMTP Username (usually your email address)
- SMTP Password
- SMTP server name*
- SMTP port*
Create the Run As Account:
First thing we need to do is setup a Run As account. This will be used later for SMTP authentication. Go to Administration > Run As Configuration > Accounts and Create Run As Account. When the Create Run As Account Wizard starts Click Next
Set Run As account type to Simple Authentication. Display name should be easy to remember and recognize. Click Next
For Credentials you would enter the account name and password you use to log into your mail provider. Click Next
More Secure, Click Create
Click Close
Once it is created Right Click on it and select Properties. Go to the Distribution tab and Click Add
Under Options select Search by resource pool name and Click Search. Select Notification Resource Pool and Click Add. Click OK
You should see Notification Resource Pool in the list. Click Apply
Create Run As Profile:
Next thing we need to do is setup the Run As Profile. In Administration > Run As Configuration > Profiles select Create Run as Profile... Click Next
Give it a nice clear name, select or create a management pack and Click Next
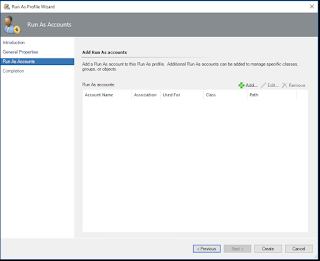
For Run As Accounts Click Add
Choose the Run As account you just created and Click OK
All good, click Create
This isn't a Run As account we will be using internally so you can disregard this. Click Close
Create SMTP Channel:
Next thing we need is to setup the SMTP Channel. In Administration > Notifications > Channels Select New > E-Mail (SMTP)... Give it a good clear name and Click Next
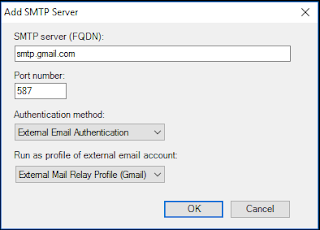
In Settings Click Add
In SMTP server (FQDN): enter the relay server information. Port number should be what was provided by your email service. Authentication method: External Email Authentication and Run as profile of external email account: should be the Run As account created earlier. Click OK
You should see the SMTP server in the list. Enter a return address and Click Next
Click Finish
From here you can setup the Subscribers and Subscriptions normally.
Next thing to do is to test it. Generate an alert and see if everything processes correctly. If it does that's great!
Now for Gmail (and probably others) there will be an additional step you need to do. After the alert was created and SCOM attempted to send the email Gmail will have blocked it. You probably got an email right after similar to this.
The wonderful people at Gmail are trying to protect your security and in doing so have blocked third party relay that is unrecognized. To allow this click the allowing access to less secure apps link.
Turn Allow less secure apps to On
Close the alerts you have in SCOM and you should start seeing the mail flow.
Common Mail Providers:
Here is a list of a few providers I found information for.
Google (Gmail):
Gmail SMTP Server Name: smtp.gmail.com
Gmail SMTP port: 587
Hotmail:
Hotmail SMTP Server Name: smtp.live.com
Hotmail SMTP port: 25
Yahoo:
Yahoo SMTP Server Name: smtp.mail.yahoo.com
Yahoo SMTP port: 587
Cox:
Cox SMTP Server Name: smtp.cox.net
Cox SMTP port: 587
Comcast:
Comcast SMTP Server Name: smtp.comcast.net
Comcast SMTP port: 587
Microsoft (O365):
O365 SMTP Server Name: smtp.office365.com
O365 SMTP port: 587
More to come!
If you like this blog, give it a g+1